9 Best Practices For Api Security
You are now 171,001+ subscribers strong. Let’s try to reach 172k subscribers by 20 September. Share this post & I'll send you some rewards for the referrals. Get my system design playbook for FREE on newsletter signup: This post outlines API security best practices. You will find references at the bottom of this page if you want to go deeper.
I created the block diagrams in this newsletter with Eraser. Once upon a time, there was a two-person startup. Yet they had only a few customers and limited features. So they ran their site using a tiny number of application programming interfaces (APIs). But one day, their site became extremely popular. So they set up a microservices architecture for scalability. Yet they knew little about API security. And sent sensitive data in plain text through the API. Also some of their public APIs often failed because of spiky traffic. Besides it became difficult to keep APIs secure as they added more features. So they researched the best practices to secure APIs. Onward. CodeRabbit: Free AI Code Reviews in VS Code - SponsorCodeRabbit brings real-time, AI-powered code reviews straight into VS Code, Cursor, and Windsurf. It lets you:
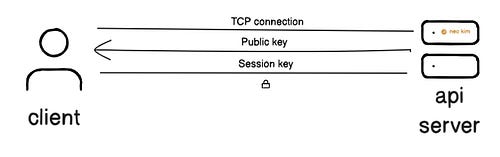
API Security Best PracticesHere’s what they learned: 1. HTTPSHTTP stands for Hypertext Transfer Protocol. Think of HTTP as a set of rules for transferring information on the Internet. But it sends data in plaintext without encryption. It means someone on the public network can easily access or change the information. Thus making it insecure. So it’s necessary to have Hypertext Transfer Protocol Secure (HTTPS) on the API. HTTPS encrypts data before sending it. Imagine HTTPS as HTTP running over an extra protocol to keep information secure. The extra protocol is called Transport Layer Security (TLS). Think of TLS as a technique to encrypt data sent between the client and server. Here's how it works:
Thus making it secure. Here are some best practices:
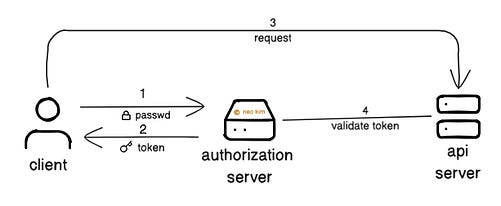
HSTS gets sent as an HTTP response header ( While strong ciphers, such as AES or ChaCha20, ensure the encrypted connection is secure. Let’s keep going! 2. AuthenticationAnybody on the internet can call a public API. Yet only verified users should access the data. So API authentication is necessary; it verifies a user’s identity before giving them system access. Here are some best practices:
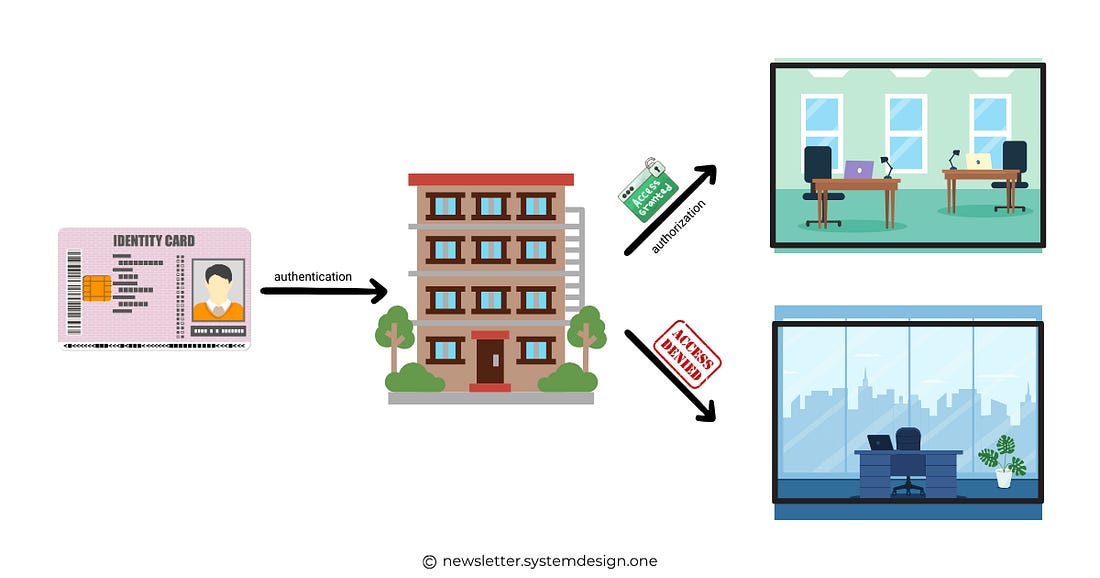
Ready for the next technique? 3. AuthorizationAuthorization decides what an authenticated client may do in a system. Imagine authentication as permission to enter a building. While authorization is like the key to enter only specific rooms once inside. Here are some best practices:
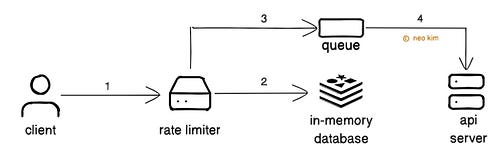
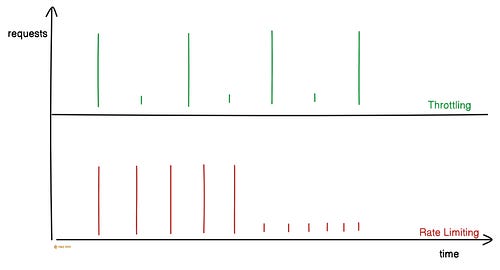
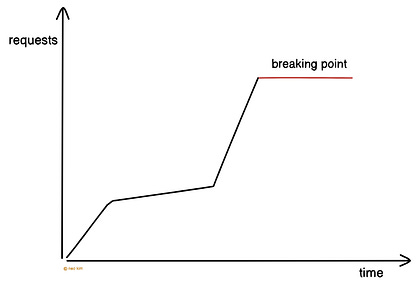
Proper access control reduces risk. So always give only the least privilege needed to get the job done. Ready for the best part? 4. Rate Limiting and ThrottlingA popular API might get too many requests at once. And this can overload the server and affect its performance. So it’s necessary to rate limit and throttle requests. Rate limiting means controlling the number of requests a client can make to an API within a time window. It protects the API from abuse. Here’s how it works:
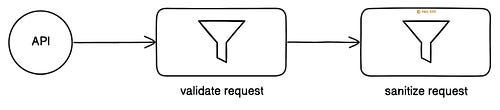
Throttling means slowing down requests instead of dropping them. It adds a delay between requests using a queue. Thus preventing server overload. Rate limits and throttling keep an API stable. Yet it has to be configured properly for a good user experience. 5. Input ValidationThere’s a risk of some requests being malformed or malicious. So it’s necessary to validate and sanitize requests before processing them. Validation checks the request structure, while sanitization removes unsafe data. Here’s how it works:
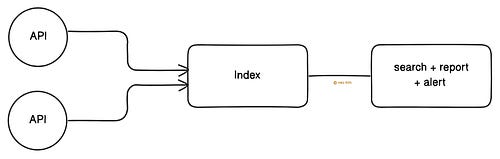
This prevents malicious scripts, SQL injections, and malformed data. SQL injection means sending malicious commands to the database via API requests. Think of it like smuggling prohibited items inside a shampoo bottle at airport security. Only safe requests should reach the system. So validate and sanitize public APIs. 6. Logging and MonitoringPrevention is better than cure. Because of this, it’s necessary to track API activity for unusual traffic or suspicious behavior. Think of it like having security cameras and alarms for safety. Here are some best practices:
SIEM collects logs from different services and analyzes them to find suspicious activity. Monitoring turns logs into early warnings. So use them to avoid API abuse before it causes damage. Let’s keep going! Subscribe to get simplified case studies delivered straight to your inbox: 7. Security AuditThere is a risk of misconfiguration and security vulnerabilities. So it’s necessary to perform security audits regularly. A security audit means checking the system to find and fix vulnerabilities before attackers exploit them. Think of it like hiring a locksmith to test all the doors in the house to ensure they lock properly. Here are some best practices:
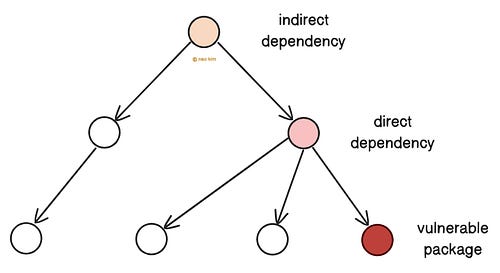
Security audits expose vulnerabilities. So use them to fix issues early. 8. Dependency ManagementThird-party code may contain hidden vulnerabilities. And a system is only as secure as its weakest part. So it’s necessary to keep libraries and frameworks up to date. Imagine APIs as a city’s traffic control system. If a traffic light fails, accidents might happen. Here are some best practices:
Ready for the best technique?... Subscribe to The System Design Newsletter to unlock the rest.Become a paying subscriber of The System Design Newsletter to get access to this post and other subscriber-only content. A subscription gets you:
|